Discover our services for
Identity security and MFA
Multi-factor authentication (MFA)
Protect your network against cybercriminals with AuthPoint! Our Multi-Factor Authentication (MFA) solution not only reduces the risk of network disruption and data breaches associated with lost or stolen login credentials, it also offers simplified configuration and management via the Cloud.
With innovative features for accurate user identification, AuthPoint goes beyond traditional two-factor authentication (2FA). What’s more, thanks to our extensive ecosystem of third-party integrations, you can extend multi-factor authentication to secure access to network, VPN and Cloud applications. Even novice users find the AuthPoint mobile app easy and convenient to use!
WatchGuard AuthPoint makes multi-factor authentication a reality.
Managing login credentials
Optimize online access security by preventing password-related threats. Securing login credentials is an essential pillar of identity protection. It ensures proactive monitoring against potential exposure on the Dark Web, while protecting users against theft and misappropriation of their login information. Given the durability of passwords, the result of two decades of technological development, their effective management remains crucial. ID management solutions provide companies with the means to strengthen their security against the risks associated with inadequate password management.

WatchGuard Corporate Password Manager
Revolutionize your password security with WatchGuard Corporate Password Manager:
Your company takes control of password security. Encourage your users to adopt robust password practices, by choosing complex and unique combinations for each required service. Thanks to seamless integration with the AuthPoint mobile application and web-based single sign-on (SSO), our service guarantees reliable protection for corporate sites and applications lacking native support for multi-factor authentication (MFA). So you can manage the quality of your passwords, reduce the need for resets, and effectively prevent the sharing and theft of sensitive information.

Dark Web Monitor
Protect your sensitive data with our Dark Web monitoring solution:
By quickly detecting any leaks of login credentials, our Dark Web Monitor service alerts you instantly, enabling you to act proactively to secure your accounts. With the ability to send targeted notifications to affected administrators and users, you can react swiftly by changing your passwords, preventing malicious exploitation and data breaches.

AuthPoint Total Identity Security
Strengthen your identity security with AuthPoint Total Identity Security, a complete solution incorporating our award-winning AuthPoint MFA technology:
Combining single sign-on (SSO), risk-based authentication and credential management via Corporate Password Manager and Dark Web Monitoring, our offering guarantees total identity protection. Offer secure access to verified users, reinforcing your company’s confidence in access management.
Cloud management

Discover the power of our secure Cloud infrastructure for seamless multi-factor authentication (MFA). WatchGuard Cloud makes managing your AuthPoint solution simple and intuitive. Our multi-tier, multi-tenant platform gives you the flexibility to easily integrate MFA authentication into your security architecture. Benefit from a user-friendly interface and an optimized access management process, including :
- Identity-based access management
- Easy user configuration
- Intelligent reporting
- Risk-aware authentication
- Rapid VPN deployment
- Dark Web Scan – Sample report
- Free Dark Web Scan included
- Cloud-based single sign-on (SSO)
Mobile application
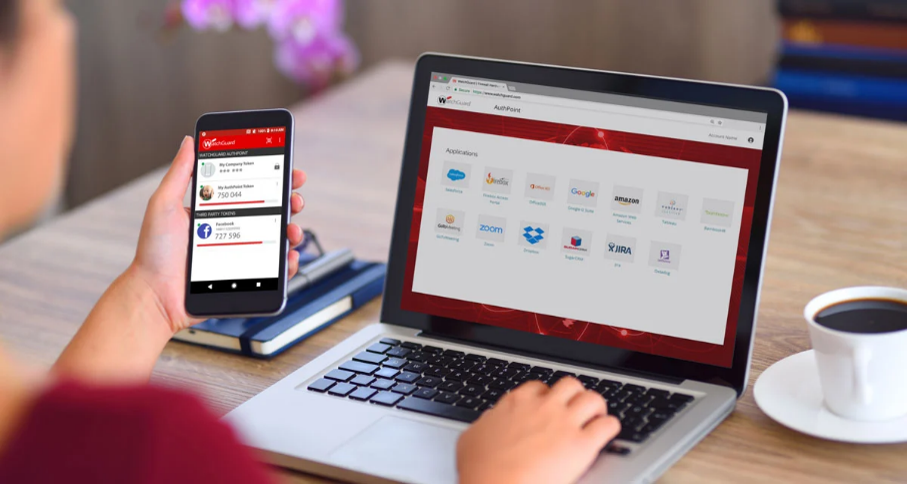
AuthPoint implements multi-factor authentication (MFA) via the AuthPoint app. Each external connection attempt triggers a push notification directly to the user’s smartphone, providing instant visibility of access attempts and their origin.
By simply accepting this notification in line with their usual process, users can access authorized network resources and Cloud applications without delay. In the event of a discrepancy, any access attempt is blocked, guaranteeing total protection against cybercriminals, even with valid login credentials.