In today’s ever-changing digital world, IT security has become a top priority for businesses of all sizes. Computer attacks are becoming increasingly sophisticated, making the protection of our data and systems more crucial than ever. At Blink iT Solutions, we’re committed to securing your business in partnership with industry leaders such as Peplink, WatchGuard, Macmon, Synology and Nakivo.
In this article, we’ll explore best practices for protecting your business against cyberattacks, highlighting solutions offered by our valued partners.

Setting up robust Fire-boxes with WatchGuard:
WatchGuard Fire-boxes offer advanced threat protection by securing your network against intrusion attacks, malware and unauthorized access attempts. By working with WatchGuard, we can help you build a strong line of defense to protect your sensitive data.

Continuous Network Monitoring with Macmon:
Macmon’s Network Access Security (NAC) management solution enables you to continuously monitor your network for suspicious activity and unauthorized devices. By integrating Macmon’s monitoring capabilities, we strengthen the security of your IT infrastructure by identifying and neutralizing potential threats.
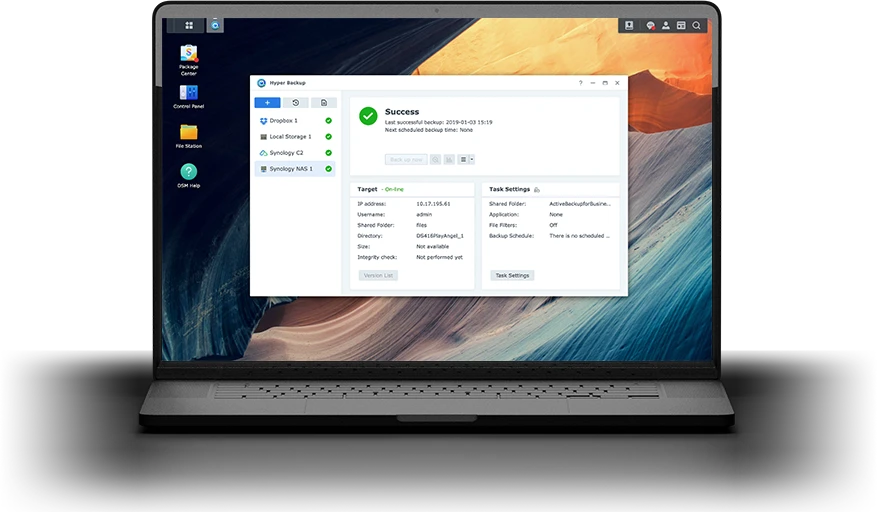
Regular, secure backup with Synology and Nakivo:
Storage and backup solutions from Synology and Nakivo offer essential protection against data loss and ransomware attacks. By implementing regular, secure backup strategies, we help you ensure the continued availability of your data and minimize the risk of catastrophic loss.

Securing Network Connections with Peplink:
Peplink routers and connectivity solutions offer advanced network connection security features, including data encryption, identity management and network segmentation. By working with Peplink, we can help you secure your network connections and protect your sensitive communications from interception and manipulation.